
Whitepaper
Security Consulting Services Overview
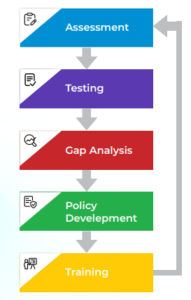
Fortify Your Business with Centelon Solutions’ Comprehensive Security Consulting Services. Our Expertise:
- Cyber Security Risk Assessment: Identify vulnerabilities and risks in your systems, processes, and controls based on ISO 27001/NIST CSF standards, and receive a clear, prioritized roadmap for remediation.
- Essential 8 Security Assessment: Measure the effectiveness of your security controls against the Essential Eight Framework developed by the Australian Cyber Security Centre (ACSC).
- ISO 27001 Compliance Assessment: An in-depth appraisal of your organization’s adherence to existing policies and industry best practices, with a focus on people, processes, and technology to meet ISO 27001 requirements.
- Third-Party Risk Assessment: Define the current and future state of your security environment in a complete Cyber Security Risk Assessment, and determine the steps needed to maintain a robust security environment as change occurs.
- Penetration Testing: Identify vulnerabilities in your IT environment using proven techniques, methodologies, and tools to detect risks.
- Phishing Simulation Risk Assessment: Measure the current level of susceptibility by performing a controlled attack against employees and identify any trends across the entire organization.
- Security Code Review: Gain insight into the real risk associated with insecure code and increase the cost-effectiveness of application security verification effort.
- PCI DSS Gap Analysis & Compliance Support: Identify gaps in your security infrastructure before a full PCI DSS risk assessment and scope the requirements for PCI compliance.
Learn how Centelon Solutions’ Security Consulting Services can help you fortify your business and meet compliance requirements.
Download Now
Centelon © 2024. All rights Reserved | Privacy Policy